
Delegates

2x Learnings from cyber security use cases: every topic from 2 companies.

User to user: direct contact to other information security experts.

Learnings, networking & emotions: a program that speaks sarcasm fluently.



Status: how secure is my company?
Challenge: what are other companies doing?
Demand: what else can I do?
Share: meet privately to discuss the current situation.
Discover: get practical knowledge from proven enterprise use cases.
Take action: be inspired by innovative solutions behind closed doors.
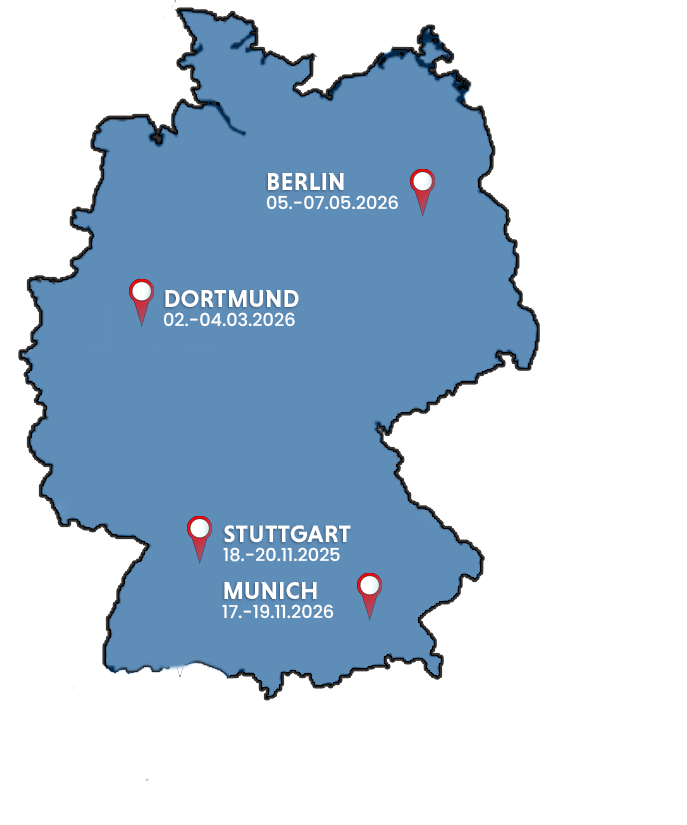
mysecurityevent 2025 – the only event where you can choose the place, the way of your participation and your own topics from the agenda.
In just 2.5 days, you can be at the heart of it all:
Start
Doors open at 5:00pm on pre-event day
Event starts at 8:30am on next two days.
Parking is available at every location.

“At the mysecurityevents on regarding cyber security, IT security experts from growth companies, medium-sized companies and corporations network and benefit from each other.”
Modern networking methods ensure take aways for delegates, e.g. duet lectures, hot seats, pitch night and audience awards directly from the community.
mysecurityevent is a meeting place for the most successful and innovative minds of the cyber security industry. It is all about content & networking. Over 2.5 days, leading information security experts share their field-tested strategies, tools and revolutionary methods in their respective fields.
Click on the ticket category of your choice and you will be redirected to our payment provider. Once there, you will enter your personal information into a secure encrypted order form and select your method of payment. After your purchase, you will receive your ticket within 24 hours. It is valid for both days and includes the preceding event.
Generally, you can choose any seat within your ticket category. Front row premium seats are reserved for VIP guests.
You will be able to upgrade your ticket to a VIP ticket at any time - as long as they are available.
You can reschedule your ticket or transfer it to a colleague, friend or loved one. Please contact us (info@mysecurityevent.com). We never charge cancellation fees. However, we reserve the right to block future events in the event of an unannounced absence.At the event we provide 5* catering, which mysecurityevent pays for you. This also includes drinks and the after show party.
At the event we provide 5* catering, which mysecurityevent pays for you. This also includes drinks and the after show party.
No, you can change this later. You will receive an automated email to enter the names and email addresses of the other participants.